How to Defend Website Against DDoS Attacks with Cloudflare : Setup & Tips
If your website is suddenly flooded with an overwhelming amount of spam traffic, you might be experiencing a Distributed Denial of Service (DDoS) attack. Such attacks can cripple your online presence, making your site inaccessible to users and potentially leading to significant losses. Understanding how to defend website against DDoS attacks is crucial for maintaining it’s stability and security.
Protecting, Debugging, and Resolving Issues with Cloudflare
This post will guide you through the steps to defend website against DDoS attacks with Cloudflare. You will learn not only how to set up Cloudflare’s robust DDoS protection features but also how to debug and resolve issues when an attack occur.
If you haven’t already configured your WordPress website with Cloudflare, please refer to our complete guide on how to set up and configure your WordPress website with Cloudflare.
Let’s get to it!
1. Understanding DDoS Attacks and How to Identify Them
1.1 What are DDoS Attacks?
A Distributed Denial of Service (DDoS) attack is a malicious endeavor designed to disrupt the normal functioning of a targeted server, service, or network by overwhelming it with a flood of Internet traffic. DDoS attacks utilize multiple compromised computer systems, including PCs and other networked resources such as IoT devices, to launch a widespread assault.
1.2 How Does DDoS Attacks Work?
A Distributed Denial of Service (DDoS) attack functions by utilizing a network of hijacked computers and devices, known as a botnet. Each device in the botnet, often infected with malware, is controlled remotely by the attacker.
These devices are then used to send a massive volume of requests to the target’s systems — be it a website, server, or network. The goal is to flood the system with so many requests that it cannot cope, leading to slowdowns or a complete shutdown, thus denying service to legitimate users.
Think of it like a crowd of people suddenly entering a small shop all at once. The shop becomes so crowded that regular customers can’t enter or receive service. Similarly, in a DDoS attack, legitimate traffic cannot reach the website because the pathway is overloaded with malicious traffic.

1.3 Types of DDoS Attacks and Their Impacts
DDoS attacks can be broadly categorized into a few types, each with unique targets and potential damages. Each type of attack has the potential to render affected websites slow or completely inaccessible:
- Volumetric Attacks: These aim to consume the bandwidth either within the targeted network/service or between the network/service and the rest of the Internet.
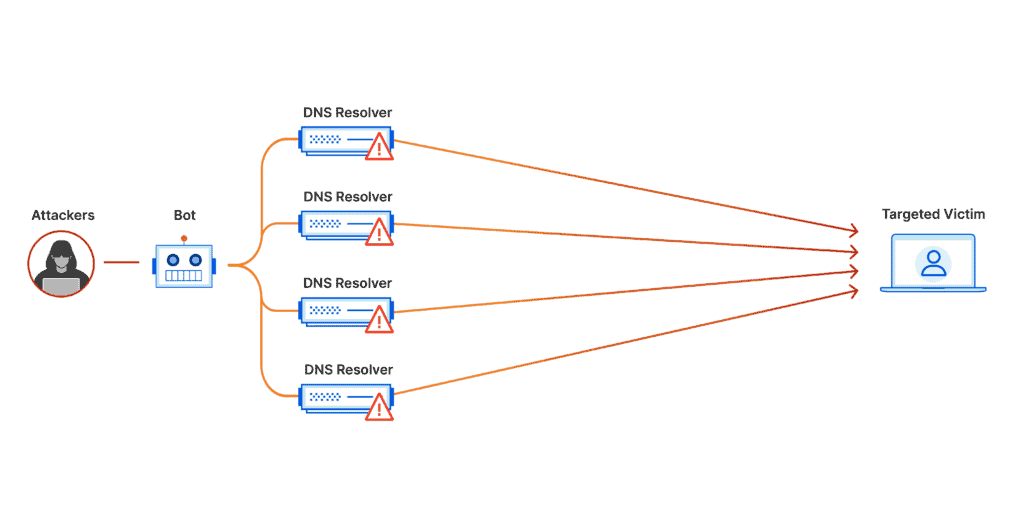
Example: UDP Flood
A UDP Flood attack sends a large number of User Datagram Protocol (UDP) packets to random ports on a remote host. As a result, the host checks for the application listening at that port; when it finds none, it replies with an ICMP ‘Destination Unreachable’ packet.
This process consumes host resources, which can ultimately make the system unresponsive to legitimate traffic.
- Protocol Attacks: These consume actual server resources, or those of intermediate communication equipment, such as firewalls and load balancers.
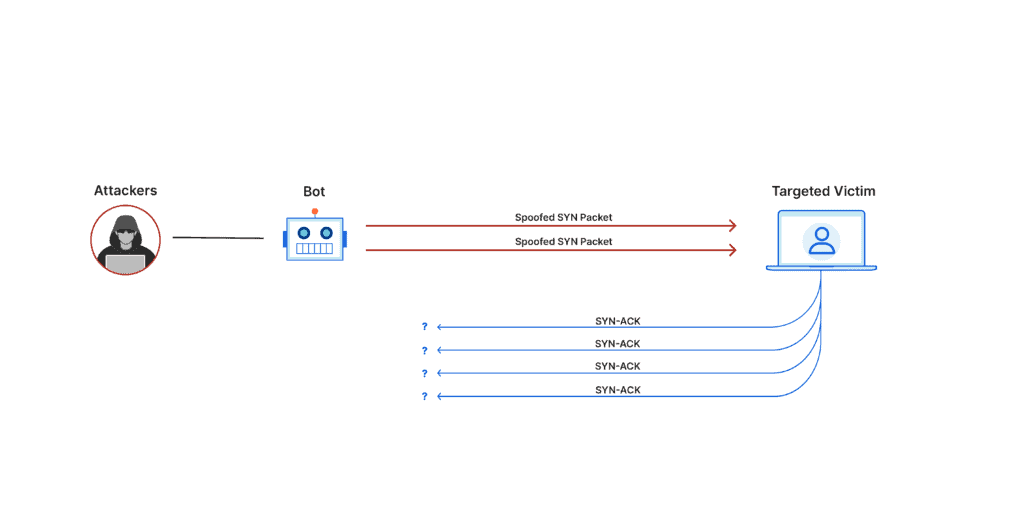
Example: SYN Flood
The SYN Flood exploits the normal handshake process of a TCP connection. Attackers send a flurry of TCP connection requests, but never complete the handshake.
This leaves the connected port in a half-open state, consuming server resources to keep this state, and eventually overwhelming the server for legitimate requests. It’s Similar to prank calling a phone number repeatedly, where the calls are never completed, tying up the phone line.
- Application Layer Attacks: These target the actual web application and are considered to involve a smaller number of requests, which are often more difficult to detect.
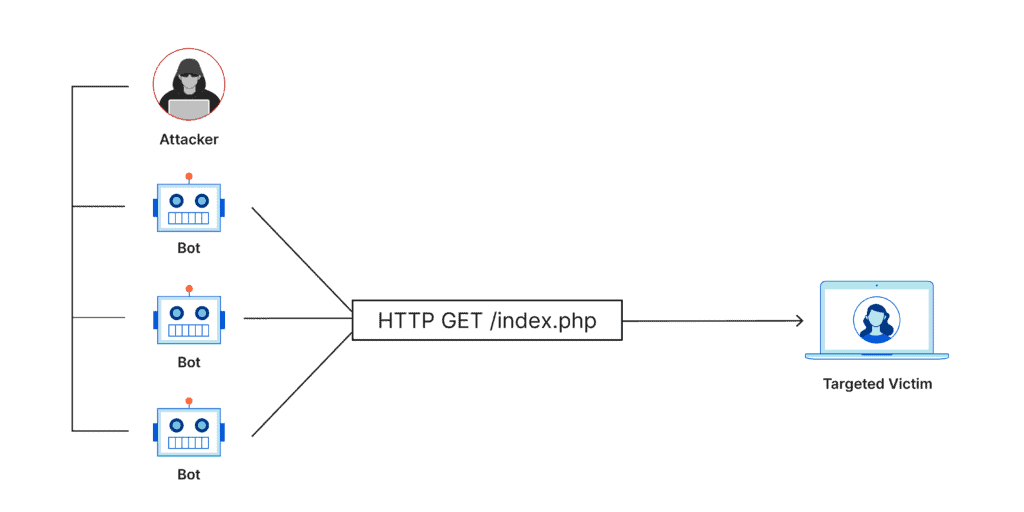
Example: HTTP Flood
This type of attack targets the layer where web pages are generated on the server and delivered in response to HTTP requests. It involves overwhelming a server with HTTP requests.
This could be as simple as continually refreshing a web page or as complex as submitting a form repeatedly. An HTTP Flood is equivalent to hundreds of customers entering a store and each asking complex questions; the workload becomes overwhelming quickly.
1.4 How to recognize a DDos Attack?
Here are key indicators that your site may be experiencing a DDoS attack:
- Sudden Spike in Traffic: An unexpected and abnormal increase in traffic could be a sign of a DDoS attack.
- Unusual Traffic From Similar Sources: If you notice a lot of traffic coming from similar IP addresses, geolocations, or device types, it might indicate a coordinated attack.
- Increased Rate of Denied Services: Frequent server timeouts or errors like 503 Service Unavailable can be caused by servers being overwhelmed by excessive requests.
- Sluggish Website Performance: A significant slowdown in website performance without a corresponding legitimate increase in visitor numbers could be due to a DDoS attack.
- Irregular Traffic Patterns: Traffic spikes at odd times of the day or patterns that do not match typical user behavior can be indicative of an attack.
- Excessive Amounts of Junk Data: High volumes of nonsensical data being sent to your server could be an attempt to overwhelm your systems.
Distinguishing between legitimate traffic and attack traffic is a critical aspect of effectively managing DDoS attacks. For instance, during a product launch, a surge in website visitors is expected; however, not all traffic surges should be treated as welcome. If traffic increases significantly due to known attackers or through unusual patterns, it’s essential to consider steps to mitigate potential DDoS attacks.
The challenge lies in accurately identifying the attack traffic without disrupting the service to real customers. DDoS attacks can be sophisticated and varied, ranging from simple single-source attacks to complex multi-vector assaults that target multiple layers of your network simultaneously.
Effective mitigation often involves deploying a layered defense strategy that can adapt to evolving threats and distinguish between harmful and legitimate traffic. Overly aggressive measures might inadvertently block genuine users, so precision in response tactics is crucial.
2. How to Configure and defend website against DDos attacks on Cloudflare
Defending website from DDoS attacks is crucial for maintaining its availability and performance. Cloudflare provides powerful tools to help safeguard your site.
Here’s a step-by-step guide on how to configure DDoS protection in Cloudflare:
2.1. Log In to Cloudflare
Start by logging into your Cloudflare account. Navigate to your dashboard where you manage your website settings.
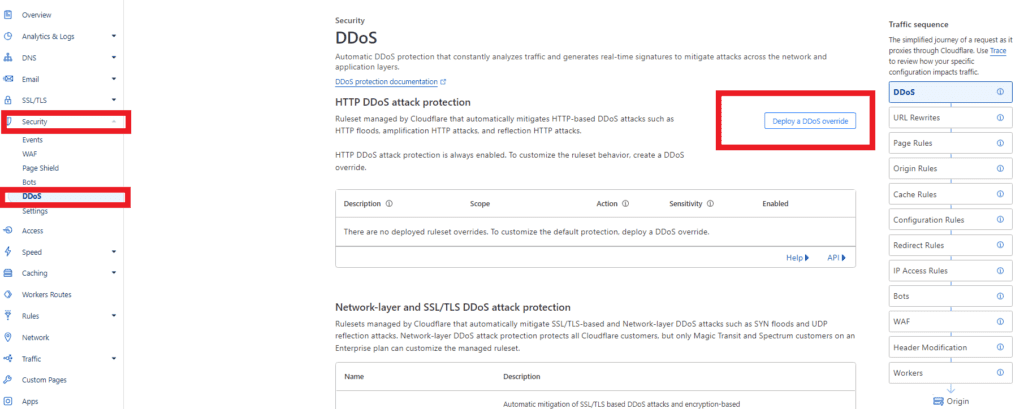
2.2. Access DDoS Protection Settings
Once you are logged in, go to the Security menu.
- Under Security Click on DDoS
- Within the DDoS tab, you will find various options to configure DDoS protection for your site.
2.3. Deploy a DDoS Override
Locate the section titled HTTP DDoS attack protection.
– Click on “Deploy a DDoS Override”. This will allow you to set specific parameters and rules tailored to your website’s needs.
2.4. Configure DDoS Rules
- Here, you can specify the details of how you want DDoS protection to function. Adjust settings based on the level of security you require and the typical traffic patterns of your site.
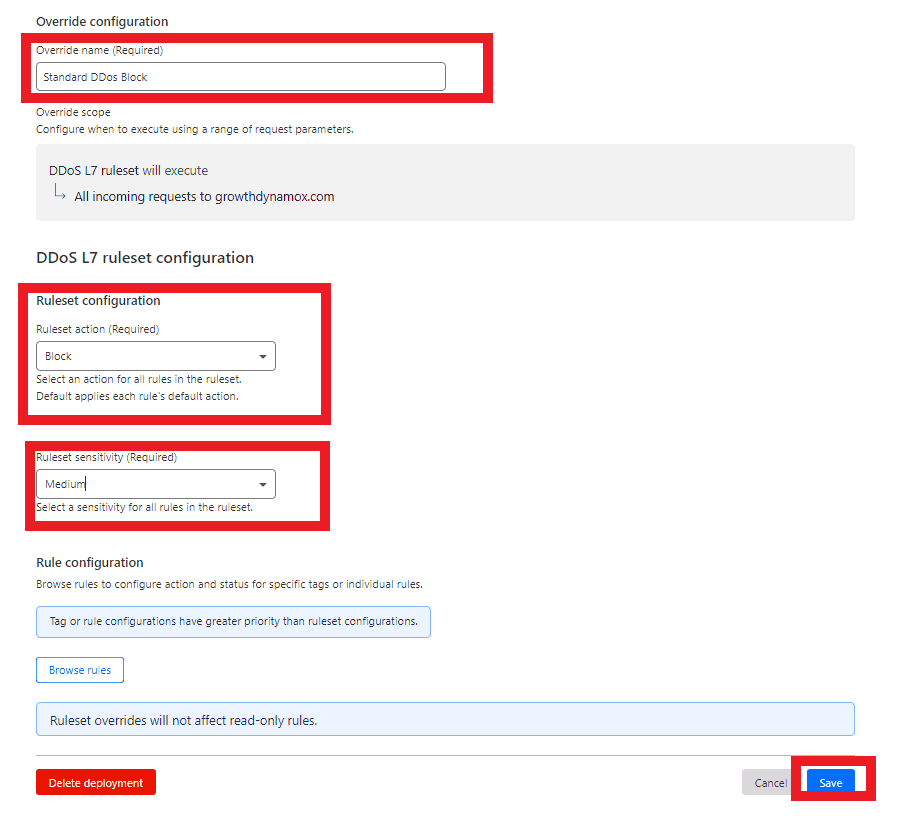
- Once you have configured the settings same as above, click ‘Save’ to apply them.
2.5. Verify Protection Is Enabled
- After saving, Cloudflare will redirect you back to the DDoS Protection page.
- Check to ensure that the Rules DDoS Protection is enabled and functioning as intended. This confirmation step is crucial to ensure that your settings are active and protecting your site.
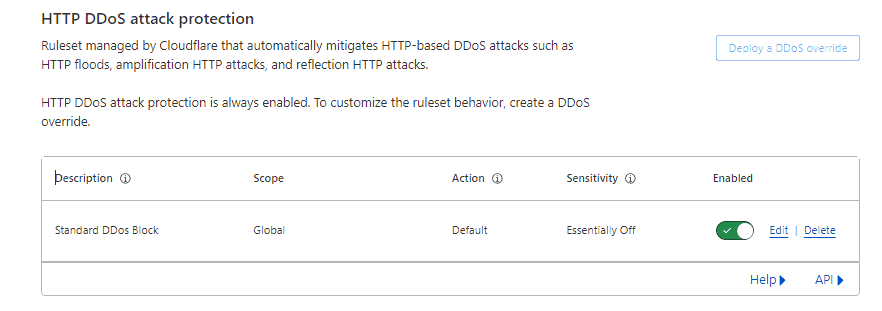
2.6. Monitor and Adjust as Needed
DDoS protection may need to be adjusted based on the evolving security landscape and your website’s changing traffic. Make adjustments if necessary.
3. How to analyze and mitigate DDoS Attacks with Cloudflare ( Advanced)
This section is tailored for Cloudflare users who encounter medium to high complexity DDoS attacks. It is particularly useful for those somewhat familiar with the Cloudflare Dashboard but who may not have extensive technical expertise.
This section will help you understand DDoS behavior, create custom firewall rules, and defend website against DDoS attacks.
Step 1: Recognize the Attack
Identify the Attack: If your website suddenly becomes slow or unavailable, and you notice unusual spikes in traffic, you might be experiencing a DDoS attack. This initial recognition is crucial for timely mitigation.
Step 2: Activate Cloudflare’s Under Attack Mode (UAM)
Navigate to Dashboard > Overview and enable “Under Attack Mode” by selecting the “I’m Under Attack” button. This mode adds an additional layer of protection by presenting a JavaScript computational challenge to filter traffic.
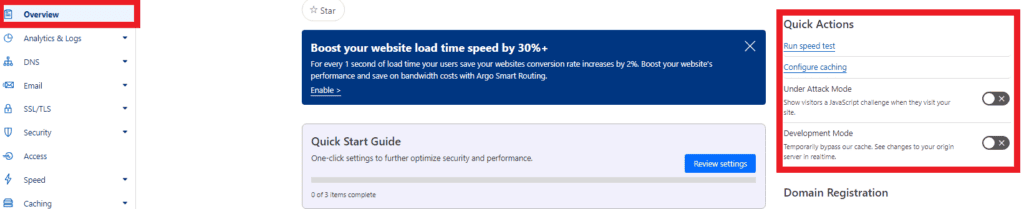
Step 3: Analyze the Attack and Formulate a Response
If activating the Under Attack mode resolves the issue, your website should return to normal. However, if problems persist or you prefer not to challenge legitimate users, further analysis and rule configuration are necessary.
Analyzing Traffic:
- Check for spikes in traffic through the Dashboard under the Analytics section:
If you see a considerable spike in the traffic, you can confirm that you are under a DDoS attack.
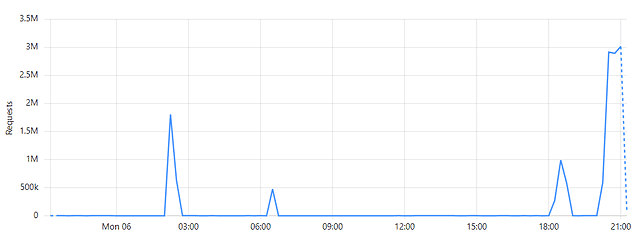
2. Observe traffic origins, focusing on any geographical concentrations or suspicious IP ranges.
Dashboard > Analytics & Logs > Requests by country section.
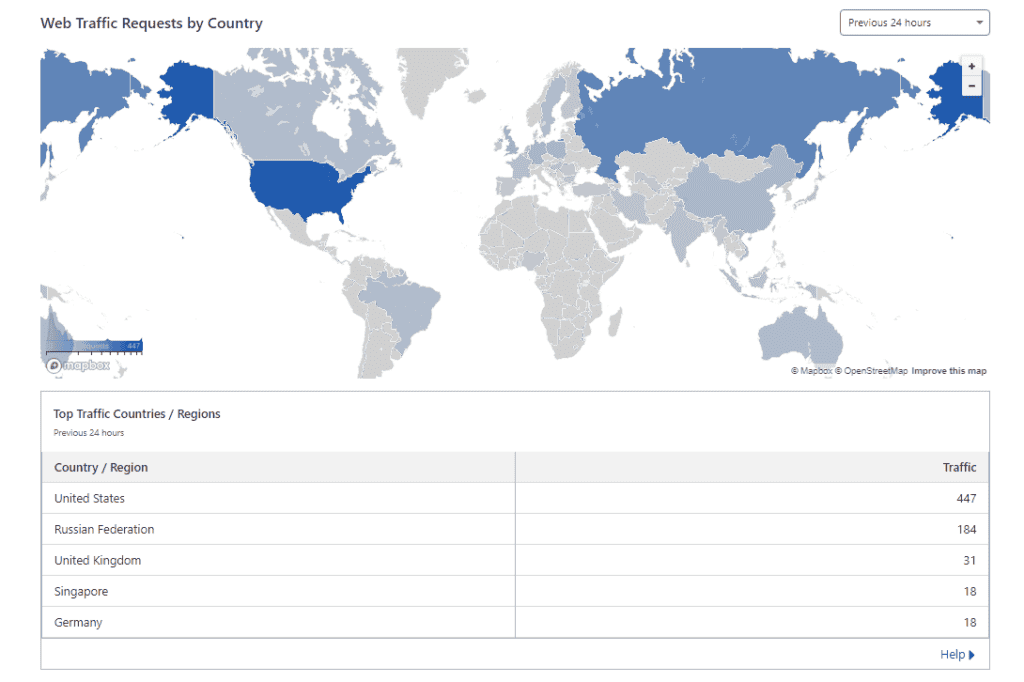
3. Assess the patterns of requests, such as the request type (GET or POST) and the HTTP version used.
Crafting Custom Firewall Rules:
- Geo-Location Analysis: From Analytics, determine if specific countries are predominantly involved in the attack.
- Request Source and Pattern: Evaluate the source of the requests and common patterns that may indicate malicious activity.
- User Agent Analysis: Identify dominant user agents used in the attack, which often provide clues about the nature of the bots involved.
Implementing Rules:
- Use the Firewall settings to create rules based on your analysis. For example, you might block or challenge traffic from specific countries or IP ranges associated with the attack.
- Consider blocking outdated or suspicious user agents that are disproportionately involved in the traffic spike.
Step 4: Deploy and Monitor Firewall Rules
- After setting up your rules, monitor their effectiveness through the Firewall > Overview tab.
- Adjust the rules as necessary based on ongoing traffic analysis and the evolving nature of the attack.
For more details and exemples on how that works, please refer to this amazing thread within Cloudflare community
Frequently Asked Questions About Using Cloudflare with WordPress
1. What exactly is Cloudflare’s “Under Attack Mode” and when should I use it?
Cloudflare’s “Under Attack Mode” is a security feature designed to protect websites during active DDoS attacks. When enabled, it introduces an additional layer of verification to distinguish between legitimate users and attacking bots by presenting a JavaScript computational challenge.
It is recommended to use this mode when your site experiences sudden, unexplainable spikes in traffic or other signs of a DDoS attack. This mode can help mitigate the attack while maintaining accessibility for real users.
2. How can I differentiate between a legitimate traffic spike and a DDoS attack?
Differentiating between legitimate traffic and a DDoS attack can be challenging. Typically, a legitimate spike will correlate with specific events such as marketing campaigns or product launches and will show diverse traffic sources.
In contrast, traffic from a DDoS attack often originates from similar geographic locations or IP ranges and follows unusual patterns, such as high volumes of traffic during off-peak hours. Monitoring tools in Cloudflare provide insights into traffic sources and patterns that can help distinguish between these scenarios.
3. What are some common signs that indicate a DDoS attack is happening?
Common signs of a DDoS attack include:
– Sudden slowdowns or inability to access your website.
– Unusually high traffic spikes uncorrelated with planned events.
– Increase in the rate of failed connection attempts.
– Analytics showing unusual traffic patterns or predominant traffic from specific IPs or regions.
– Repeated hits to the same endpoint or URL in rapid succession.
4. Can Cloudflare automatically mitigate all types of DDoS attacks?
Cloudflare is highly effective at mitigating many types of DDoS attacks, especially volumetric attacks, by distributing traffic across its vast network.
However, more sophisticated multi-vector DDoS attacks may require additional manual configuration and monitoring to fully mitigate.
Cloudflare provides tools for creating custom firewall rules and settings that can be tailored to defend against complex attack patterns.
5. What steps should I take if my website is still experiencing issues after enabling DDoS protection on Cloudflare?
If issues persist even after activating DDoS protection, consider the following steps:
– Review your Cloudflare security settings to ensure that all configurations are optimized for your specific traffic and security needs.
– Analyze the firewall and security event logs in Cloudflare to identify any patterns or remaining vulnerabilities.
– Adjust your firewall rules to more precisely target and block malicious traffic.
– Contact Cloudflare support for assistance with advanced threats.
– Continuously monitor traffic and adapt your security settings as new threats emerge.
Conclusion
Successfully configuring Cloudflare to defend website against DDoS attacks is a critical step in safeguarding your WordPress site. However, the foundation of any secure website begins with robust and reliable hosting. By choosing a hosting provider that offers advanced security features and optimized performance for WordPress, you can further enhance your site’s resilience against cyber threats.
If you’re looking to upgrade your website’s hosting environment, we invite you to explore our range of hosting plans designed specifically for WordPress websites. Our plans not only provide enhanced security and performance but also integrate seamlessly with Cloudflare’s protection services, ensuring your website remains fast, accessible, and secure at all times.
Discover our hosting solutions today and give your WordPress site the robust foundation it deserves.